Teaching
I. STUDENT EVALUATION
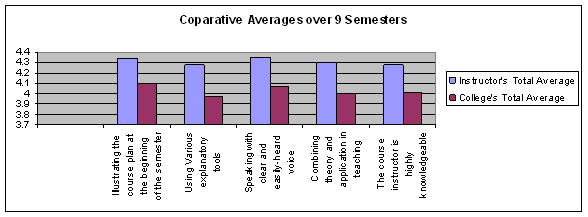
The following is a summary of the student evaluations for courses I taught for each semester. The table below illustrates comparative statistics using averages based on a sample of all sections I have taught over the last 9 semesters.
| Comparative of Averages Based on 9 Semesters | ||
| Instructor's Total Average |
College's Total Average |
|
| Illustrating the course plan at the beginning of the semester | 4.33 | 4.10 |
| Using Various explanatory tools | 4.28 | 3.98 |
| Speaking with clear and easily-heard voice | 4.34 | 4.06 |
| Combining theory and application in teaching | 4.30 | 4.00 |
| The course instructor is highly knowledgeable | 4.28 | 4.02 |
II. TEACHING LOAD
1. Teaching Load
| Course | Number of Sections | Credit Hours | Term |
|
2 |
12 |
Fall 2003 |
|
2 |
12 |
Spring 2004 |
|
2 |
9 |
Fall 2004 |
|
1 3 |
12 |
Spring 2005 |
|
2 |
12 |
Fall 2005 |
|
1 |
12 |
Spring 2006 |
|
2 |
9 |
Fall 2006 |
|
3 |
9 |
Spring 2007 |
|
1 1 1 |
9 |
Fall 2007 |
|
1 1 1 |
12 |
Spring 2008 |
| Total | 108 | ||
2. Courses Taught
Since 2003 I have taught 10 different courses. Following is the list of the courses I have taught:
- ITBP210 Communication Fundamentals
- ITBP 209 Digital Hardware Fundamentals
- SEC301 Security Principles and Practices
- ITBP 330 – Cryptographic Algorithms and Protocols
- SECB 351 Access Control Models & Technologies
- SECB358 Network Border Control
- SEC451 Policy, Criteria and Evaluation
3. Courses that I can teach
There are many courses available in the CIT curriculum that I can confidently teach which are listed below:
- ITBP119 Algorithms and Problem Solving
- ITBP211 Computing Systems
- ITBP300 Computer Architecture
- ECBP324 Networked Operating Systems
- SECB405 Secure Protocols for the Internet and Ecommerce
- SECB408 Secure Mobile Code
- ECBP411 Mobile Commerce
- ECBP430 Electronic Payment Protocols
- NEBP461 Computer and Network Security
- NEBP470 Network Design and Implementation
- NEBP471 Network Management
4. Courses that I have coordinated
The table below shows the list of courses that I have coordinated in the CIT.
| Code | Title | Semester |
| SECB301 | Security Principles and Practices | Fall 2004, Spring 2004 , Spring 2005 |
| SECB 358 | Network Border Control | Fall 2004 |
| SECB 351 | Access Control Models & Technologies | Spring 2006 |
| SECB 451 | Security Policy Criteria and Evaluation | Summer 2007 |
III. METHODOLOGY AND DOCUMENTATION OF TEACHING PROCESS
This section includes documentation on the teaching process and contains a sample of course portfolio and a sample of course development.
1. Course portfolio
The course portfolio of SECB 351 – Access Control Models & Technologies. It contains:
- Course syllabus
- Teaching material
- Quizzes & Tests
- Midterm and Final exams
- Home work assignments
- Course development report
- Course assessment
IV. CONTRIBUTION TO PROGRAM AND COURSE DEVELOPMENT
I have been involved in the development and the update of many courses in the security track. Following is a list of some of the courses that I have contributed to their development:
- Participated in the restructuring of the security new curriculum. I assisted the track coordinator in removing, merging, and renaming some of the old course in order to meet the CIT new policy for reducing the total number of each track’s courses to ten courses.
- SECB 301- Security Principles and Practice: I have fully developed this new course in Spring 2004
- SECB358 – Network Border Control: I have fully developed this new course in Summer 2004
- SECB 351- Access Control Models & Technologies: I have fully developed this new course in Spring 2005
- SECB 451- Security Policy Criteria and Evaluation: I have fully developed this new course in Spring 2006
- SECB 425- Security Architectures and mechanisms: Assisted in the development of this course by providing the developer with a topical outlines, material to be included in this course and recommended a textbook for these courses.
- NEBP461 – Network Security: I have contributed to the development of this course by discussing with the developer the security topics that should be included in this course.
I have also been involved in the development and update of many hands on labs.
Following is a list of some of these labs that I have contributed to their development:
- Initiated and led the establishment of the Sun-CIT Center of Excellence for research
- Co-developed SECB 301 Lab (Spring 2004)
- Co-developed SECB358 Lab (Summer2004)
- Leading the wireless security lab
V. USE OF AND DEVELOPMENT OF MODERN TEACHING METHODS
This section describes the course development methodology that I have followed. I have chosen the SECB 358- Network border control as an example to illustrate my adoption of Active and Cooperative Learning techniques in my classrooms. To provide such protections, students must learn what is known as the defense-in-depth concept, which is a layered approach that includes the integrations of software, hardware, administrations, and human factors.
This course was designed to provide some theoretical concepts and practical means for designing, deploying, and maintaining network perimeter defenses. It discusses perimeter components such as firewalls, virtual private networks (VPNs), routers, intrusion detection systems (IDSs), and authentication servers, and explains how to integrate them into a unified whole to meet real-world business requirements.
The lab of the course was designed to provide the students with needed skills and hands on knowledge needed for router security configuration, applying security to network design, Firewalls and VPNs.
This development of this course focused on the use of active learning methodology to enhance students’ critical thinking and problem solving skills. It was designed to be delivered in the form of two 2-hours interactive sessions every week (4 hours in total). One of the two sessions (2 hours) is devoted to class room lecturing/active learning and the other session is devoted to a hands-on lab part.
The classroom part:
In the classroom part, every class session was structured according to the Book End active learning approach, which includes following:
- Advance organizing: In this part, the faculty starts the session by finding out how much the student know about the topic to be learned in that session. In this part, the faculty will utilizes the information he/she prepared before hand, divides the class room into a reasonable (heterogeneous) groups, and invokes a discussion session by either asking a question that the student try discuss among them selves and then answer collectively, or by introducing a problem/real life scenario that the students can also discuss and try to solve.
- 3 to 4 minutes (turn to partner) discussion: during this 3 to 4 minutes, the students will first formulate their own responses to the faculty's question/problem, share their responses with the group members, listen to their group member's responses and then the each group create one response to the faculty's question/ problem.
- Lecture: Once the groups provide the answers, the faculty follows that session with 10 to 12 minutes lecture, formalizing the concept and explaining the experts' opinion regarding the given topic. This process gets repeated every 10-to-12 minutes.
- Session Summary (Minute Paper):
Every class session is concluded by a short questioner, given to the students to get their feedback on what they have learned and to assess what needs to be explained further in order to improve the learning process in future sessions
Further more, the course was also designed to incorporate some Problem Based Cooperative Learning Format. In this approach, the students will be given some small tasks, or problems, then solicit one set of answers from the group, allowing them to strive for agreement, but making sure that everyone is able to explain the strategies used to solve each problem.
Formal Cooperative Learning, via working on group projects, was also incorporated in this course. in this format, students are assigned to groups of 3 to 4 members, and With the help of the lecturer, students select a network-security technology/concept of their choice, conduct a thorough technical research on the chosen security technology/concept, write one repot, and prepare and deliver one presentation for their class mates.
Finally, some Peer reviews are conducted at least twice during the semester. In this type of review, an arrangement with another fellow faculty will be made to come and observe the lecture, to stay with the students after the lecture to listen to their feedback on the lecture and on the overall teaching style of the lecture, and then discuss the outcome of the visit with the lecturer. This will be used to improve class room teaching by utilizing the constructive feedback from the visiting fellow faculty.
The lab part
The lab session is focused on interactive sessions were the lecturer, instructor, and students are working together on hands-on lab exercises in a collaborative, cooperative, and interactive teaching-learning environment .The lab of the course will provide the students with needed skills and hands on knowledge needed for router security configuration, applying security to network design, Firewalls and VPNs.
VI. PREPARATION OF APPROPRIATE EXAMINATIONS
The following is a list of evaluation tools used for assessing students:
- Quizzes: Are used to assess student after the completion of each chapter. This type of assessment is made of a mix of multiple choices, true or false, or a short answers types of question. They are typically used to gauge the level of understanding of the students for the topics discussed and help me adjust my teaching style accordingly.
- Home work assignments: Are usually given to students on weekly bases to keep them actively involved with the course, even when they are not in class. These assignments are usually composed of some exercises assigned from the text book, or some small internet based type projects that require the students to research the information themselves.
- Term Projects: Projects are one of the main assessment tools I use for evaluating the students. In most courses, students are given group projects to address relevant topics that are not covered or covered lightly in the class. Depending upon the size of the class, groups are used made of two to three members. Typical deliverables for a group project include researching a topic of their choice, conduct a reach to address specific problem area, write a short report, and provide a power point presentation of their topic to the entire class. The main objectives behind these projects is to help students learn how to conduct meaningful research, to encourage team work among the students, to help them develop their writing skills, and to prepare them for the real life work environment where they have present their work in a professional manner. The following is a sample list of proposed projects topics:
- Operating Systems Security
- Firewall
- Viruses/Worms &Trojan horse
- Security in wireless networks
- Authentication and Access Control
- Home network security
- Biometrics
- Watermarking
- Midterm and Final exams: These assessment tools are standard evaluation tools and they are usually required by the university and conducted on predetermined dates.
5. Lab experiments: In the courses that contain lab as part of their structure, hands-on, lab assessments are usually required and conduct inside the lab, by the lab instructor.
VII. INTERACTION WITH STUDENTS
As previously indicated, a adapting and Active and Cooperative Learning approach in my class forces the students to be fully involved in the learning process and in order for this approach to be effective, the class instructor must also be fully involved and prepared before hand, through the development of some scenarios and questions to invoke students participations and discussions inside the classroom.
VIII. STUDENT SUPERVISION
Since I joined the CIT I have been continuously supervising students for projects in various capacities. The following lists and describes the projects that I have supervised:
1. IT Core Projects
- Supervised a group of 4 (female) students in their junior exhibition project.
Project Title: Acronyms Translator System
Group Members: Maryam Abdulla Al Mazroooei 200511606
Badreyah Saleh AlSaadi 200511700
Fatmah Saleh Hashmi 200511770
Sawasan Rashed Mobarak Yammahi
Semester: (Spring 2008)
- Supervised a group of 4 (female) students in their junior exhibition project (IT-Core)
Project Titled: Single Sign On
Group Members: Mouza Saqar Baloushi 200414250
Salwa Ali Ahbabi 200414241
Shaikha Nasser Nuamimi 200414253
Latifa Saeed Shamsi 200413635
Semester: (Fall 2007)
2. Senior Exhibition
- Supervised 4 different (female) students in their senior exhibition project.
Project Title: Performance analysis of the Juniper firewall
Group Members: Abeer A. Al Banna 200323687
Mariam A. Zaabi 200314306
Maryam M. Al Naqbi 200312695
Safa M. Hashmai 200324545
Semester: (Spring 2008)
- Supervised 5 different (female) students in their senior exhibition project.
Project Title: The Impact of the Access Control List's Size and order on the Performance of the Router-Based Firewalls
Group Members: Najat Awn 200105096
Aysha Kaabi 200202201
Aysha Sultan 200203124
Jalila Sultan 200105091
Mutea Salem 200105018
Semester: (Spring 2007)
- Supervised 4 different (female) students in their senior exhibition project.
Project Title: Impacts of security in WLAN
Group Members: Aamal Al Tenaiji 200105051
Meera Al Mansouri 200105422
Huda Al Khezaimy 200002031
Hanadi Al Suwaidi 200002304
Semester: (Spring, 2006)
- Supervised 4 different (male) students in their senior exhibition project.
Project Title: Implementation of BS7799 for Dubai Holdings
Group Members: Waleed Ahmad Al-Ali 200101521
Saleh Hassan Al-Ali 200101719
Khalid Al-Hammadi 200000259
Ahmad Al-Ansari 200000201
Semester: (Spring, 2006)
- Supervised 4different (male) students in their senior exhibition project.
Project Title: Implementation of Firewall solution for (Commercial) multi-domain Environment.
Group Members: Mohammed Ahmad Al-Marzougy 200101455
Hamed Abubaker Raeesi 200101598
Salem Ismail Al Hashemi 200101532
Omar Mohamed Darwish 200101573
Semester: (Spring, 2005)
- Supervised 3 different (female) students in their senior exhibition project.
Project Title: Implementation of Firewall solution for (military) multi-domain Environment.
Group Members: Noura Haider 200105188
Sheikha Hefaity 200105301
Hajar Hosani 200105238
Semester: (Spring, 2005)
3. Internship supervision
- Supervised 5 different students in their internship program (UAEU IT Center,, Fall 2004)
- Supervised 5 different students in their internship program (UAEU IT Center, Fall 2005)
- Supervised 1 students in her internship (Al Maraq Hospital, Fall 2006)
- Supervised 5 different students in their internship program at the University IT Center (UITS), (Fall 2007)
IX. CONTRIBUTION TO EDUCATIONAL CONFERENCE
We have done some work to develop some learning techniques using game playing. This work have lead to publishing o f the paper listed below.
- Emad Eldin Mohamed and Ezedin Barka. PLAYING CRYPTOGRAPHY: AN E-LEARNING APPROACH. The 9th International Conference on Interactive Computer Aided Learning ICL 2006. Villach, Austria. 27 – 29 September, 2006
